Bug Bounties Part 1
I think it's great that companies have started programs to reward ethical hackers that responsibly disclose vulnerabilities before they become a problem to their customers. Each of the vulnerabilities that I will be posting has already been fixed by the group responsible, or the site has been retired. I'm publishing this information because it was an interesting exercise to find these vulnerabilities. I think that by examining previously found vulnerabilities, we can determine patterns that can help reveal vulnerabilities in the future.
Vark.com
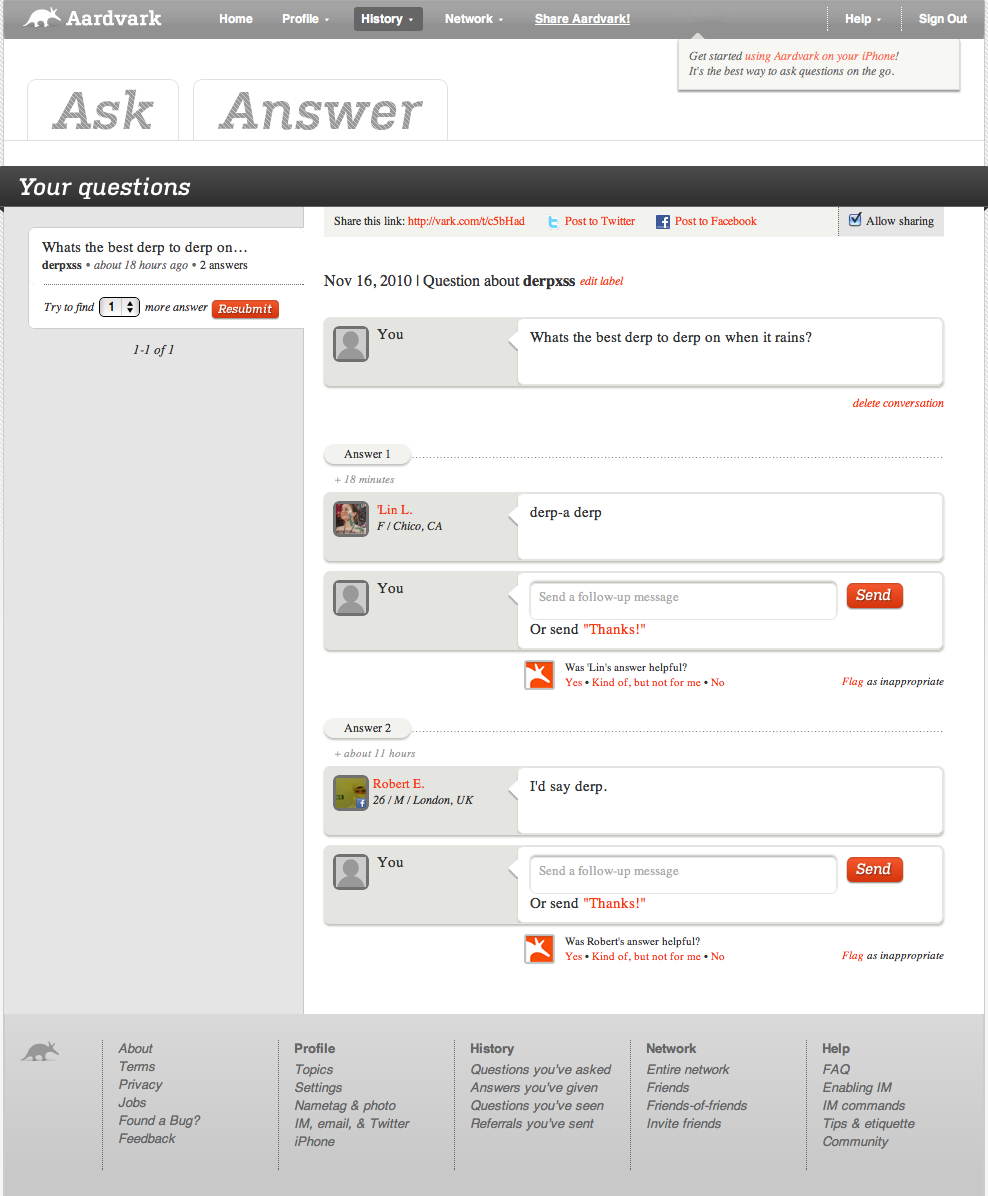
One of the first bug bounties I received was for the website "vark.com". Vark.com was a site where users can ask questions, and Vark would find users with knowledge of that topic to answer the question for you. It's pretty cool concept, one that's been done a few times before.
Vark had XSS on the main search query field:
[code autolinks="false"]http://vark.com/users?q=xss%C0%3Cimg+src=x+onerror=alert(1)//&commit=Search[/code]
The cool thing about this attack vector is the characters "%C0%3C" or 0xC03C. If you are unfamiliar, this is an attack on improper decoding of UTF-8 characters. UTF-8 is a variable-width encoding allowing for text characters to be represented by multiple bytes of code (eg. Latin Capital Letter A with Grave À is represented with 0xC380. A funny thing is that there are no characters between 0xC000 and 0xC1FF, even though it falls within the UTF-8 range. A parser that wasn't running correctly could interpret 0xC03C as one character, allowing it to pass a filter against 0x3C ("<"). When a secondary parser or web browser sees an invalid UTF-8 encoding, it will simply ignore the invalid character ("0xC0") and you are left with 0x3C, and the ability to insert malicious code.
The same parsing issue allowed for XSS on new questions that would be viewed by other users.
Google paid out $500 for this vulnerability. Vark.com has since been discontinued.
Jaiku.com
Jaiku was a twitter clone that Google purchased in 2007, and re-launched in 2009 after being brought into the Google development eco-system.
I found XSS on the page that you get after registering for the system. Incidentally, the page could also be visited by users that were not logged in, or users that had been logged in for a long time.
[code autolinks="false"]http://www.jaiku.com/welcome/done?redirect_to=javascript:alert%281%29[/code]
The redirect_to URL was reflected in a link.
Jaiku was losing popularity and with Google Buzz and Google+ initiatives alright out there, it was likely to be shut down soon. However, the Google Security Team told me that there were still quite a few diehard Jaiku users around, and so they paid out $500 for the vulnerability.
Google retired Jaiku.com on January 15, 2012.
spreadsheets.google.com
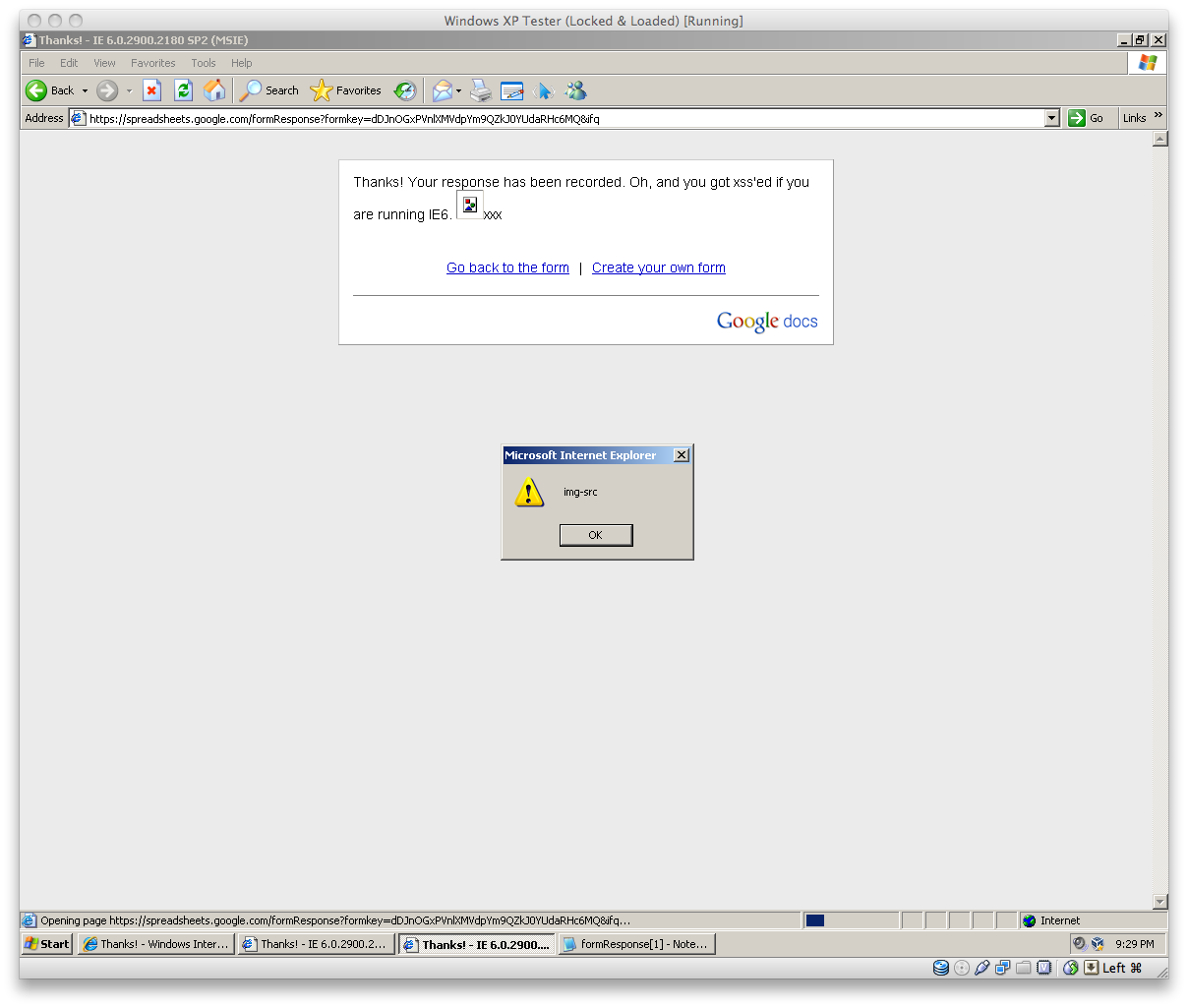
Google Docs has functionality to create surveys for people to fill out and provide information. The extended description for a survey allowed a user to enter in some HTML elements. Additionally, there is a feature to edit the confirmation page that is presented once the survey is completed, and an attacker could include some HTML here as well. Google has a really comprehensive filter against XSS here, where they actually allow users to enter certain HTML elements (like images, styling, etc). At the time, Google docs didn't seem to be using the latest version of this filter.
The XSS is exploited using <IMG> tag with a "src" attribute set to execute javascript, a vulnerability that affects Internet Explorer 6:
[code autolinks="false"]<img src="javascript:alert('img-src')">xxx</img> //xss[/code]
You can still go to my POC that I sent in to google security, and if you look at the source code of the page you'll see what their filter is now doing to prevent XSS:
[code autolinks="false"]<img src="//images-docs-opensocial.googleusercontent.com/gadgets/proxy?url=javascript:alert(document.domain)&container=docs&gadget=docs&rewriteMime=image/*" /> //xss[/code]
Google sent me a $500 check for reporting this vulnerability.